Unfortunately for all of us, our mental image of the typical phishing scammer is not even close to reality.
You probably think of a person sitting in dark room in front of multiple glowing computer screens, furiously writing code to craft their attack. They’re a lone wolf operating in the deepest, most inaccessible corners of the web.
According to a new security report from Akamai, this is picture is pretty much totally wrong.
What phishing REALLY looks like behind the scenes
Phishing has become a service industry—complete with virtual storefronts, full-product suites, service tiers, and checkouts that take Pay-Pal.
What you find in these shops are phishing kits for sale. These are virtual equivalents to a crafting kit you’d buy at Michael’s or Joann’s. Even if you don’t know how to build it yourself, the kit comes with all the pieces and supplies you need to create what’s pictured on the box—coding skills not required.
Nefarious developers build kits so criminals can send emails that appear to come from Amazon, Google, Netflix, Microsoft Office, or PayPal and many more. The purchaser can pay by the user and by the month. Stores even offer mailing service options to overcome email security filters, such a priority settings, encryption, and using random sender names and email addresses.
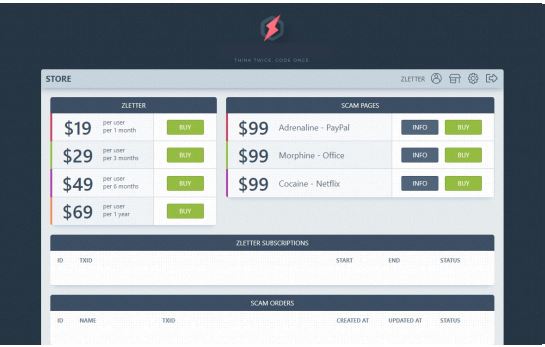
But wait, there’s more!
If all of that wasn’t enough, these kits even include free updates and multi-language support. Plus, they often include a data dashboard so the buyer can see how their phishing campaign is working and make adjustments if needed.
Why so much effort? Because every.single.piece. of information criminals can get from you is sellable.
It doesn’t matter what data it is, there’s a market for it. And it’s not just about getting new information from unsuspecting victims. Akamai’s experts say it’s also about verifying the accuracy of what’s already out there.
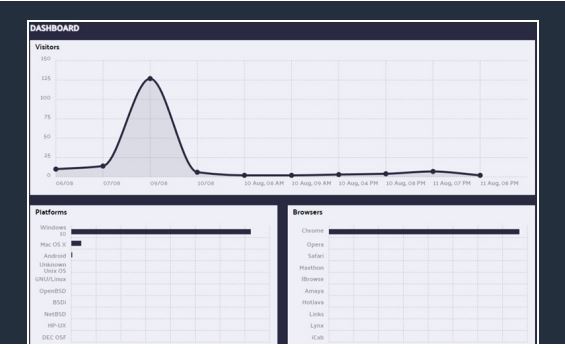
The good news
Phishing is lucrative enough that it has evolved into a rather sophisticated online marketplace. However, despite the slick storefronts, phishing attacks—no matter how well run—rely on human psychology to work. That means that you can stop phishing attacks if you stay vigilant. Here are 5 fast tips:
- Don’t be complacent. No two phishing attacks look alike. The bad ones with grammar errors and misspellings are easy to spot, but the good ones are super subtle because they’re tailored just for you. If it doesn’t feel right but you don’t know why, trust your gut.
- Remember: companies you do business with already have your information. Scammers know you want to be helpful and don’t want to lose services. That’s why they’ll craft emails asking you to verify your information, re-enter payment information, etc. Don’t fall for it—any above-board company should already have you in their systems (and if there was a catastrophic loss or issue, you would have heard about it elsewhere).
- Don’t click! If an unsolicited email tells you that you need to click on a link to take action immediately/urgently, don’t do it. That link can download malware onto your machine or direct you to a legit-looking webpage that’s only there to harvest information from victims.
- Don’t fall for threats. This is another common psychological trick scammers use to fluster you into acting without thinking. The minute you read that an account could be closed/compromised or that urgent/immediate action needs to be taken, you should imagine red flashing lights and blaring sirens. Look up a number for the business (don’t use one provided in the potential scam email) and call if there is any question.
- Check the details. Look at the sender email address. Review that link address by hovering over it (and if you click on it, double check it’s taking you to the real site in the browser address). Scammers can fake a lot of things, but not everything. Want more tips? Be sure to check out this infographic:

If you think you fell for a phishing scam, you’re not alone—but do take action to control any potential fallout.


